Bita Beigishah
If you’re thinking about a career in cyber security, you would do well to acquaint yourself with a Linux distribution known as Kali. This particular distribution has been tailored for penetration testing and comes with all kinds of tools and features for cyber security professionals. I’ll get you started with installation, guide you through some of the tools, and tell you how to practice hacking legally.
Warning: It is highly illegal to hack a computer system/network that you do not either own or have explicit written permission to hack. If you get caught using these tools for malicious reasons you will face multiple felonies.
How to Install Kali Linux
There’s no sense in explaining these tools if you can’t follow along with me right? To download Kali Linux visit the official Kali Linux website, and choose the appropriate download. If you want to run Kali on a VM (virtual machine), download the Kali virtual image.
For those installing Kali onto a hard disk, check out the official install guide. If you’re running a VM, follow the instructions specific to the hypervisor of your choice. Once Kali is up and running, you will see a screen with several options available. Leave the topmost section highlighted, hit enter, you should go straight to the GUI desktop. At some point you will likely need the default credentials:
- Username: root
- Password: toor
You should really change both of these. You don’t want to get in the habit of leaving default credentials for any system. If I was to try and gain access to a Kali system, you better believe I’ll be trying root/toor first! Don’t forget that Linux is case sensitive! I’d also advise that you make a second account with limited access. If you’re lost, you might want to read up on the basics of Linux before moving on.
Kali Tools: Wireshark, Metasploit and Armitage
It can be pretty daunting to figure out what tools to start with in Kali. After all, there are over 600 tools in a standard installation. I’m going to start you off with just three tools: Wireshark, Metasploit, and Armitage.
Wireshark
For an ethical hacker (or any hacker really) the information gathering stage is essential. Wireshark is essentially a packet/protocol analyzer. With this tool you can collect information from a remote PC to save and analyze later on. You can even use Wireshark to de-crypt SSL and TLS packets. For now I just want to get you familiar with the interface.
Go ahead and open up Wireshark by typing wireshark into the terminal and pressing enter. At this point if you haven’t made a secondary user account, it’s going to yell at you a couple times about using Wireshark while logged in as root. You can either click to continue or take their warning seriously. I’d choose the latter. On the main screen simply double click on the name of your network adapter, it’s most likely eth0 or wlan0 but it may vary according to your setup. Click on the adapter, then select capture from the top menu, and click on start directly above the interfaces. (See the image below).
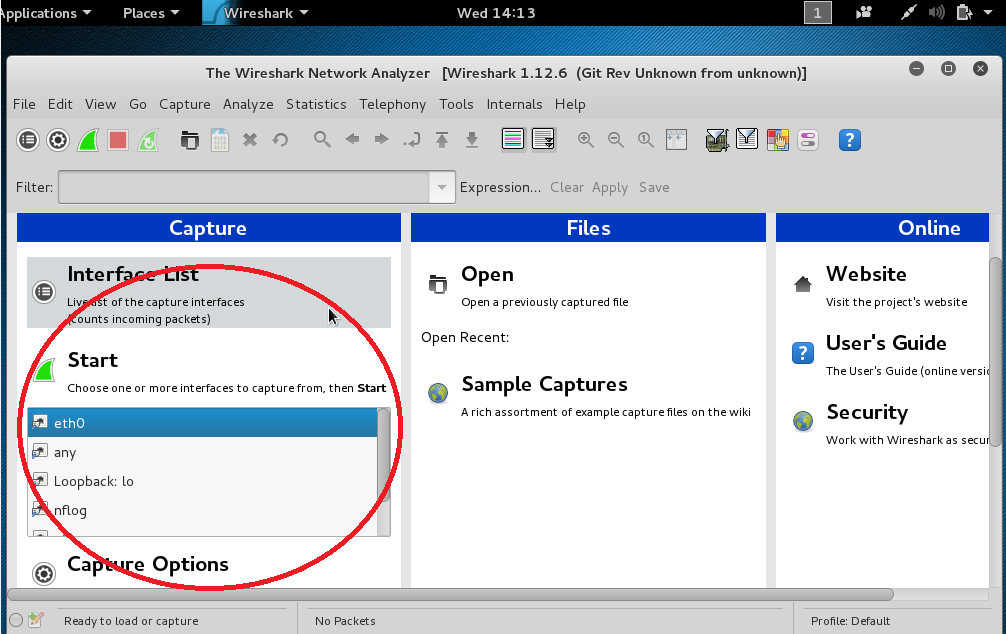
Wireshark has now changed to a view with three windows of information and is scanning for traffic. You may have to re-size the windows to read information appropriately. Now navigate to a website of your choice to generate some packets. The Wireshark window should now be filled with captured packets.
Find and choose a TCP packet. Notice the source, destination, and info columns. Under the information column you should see something like the following: 443→36286 [ACK] Seq=1 Ack=183 Win=65535 Len=0
This says that port 443 is communicating to port 36,286. In this case port 443 is the common port on a server, while 36286 is a random port opened up by your computer. ACK refers to the TCP/IP sequence. You don’t need to worry the remaining details right now.
The bottom pane of Wireshark shows the contents of the packet. Encrypted communications like SSL and TLS will show up as gibberish. In the clear communication, such as HTTP and FTP packets, will generally have some information that you can read. Use the filter at the top of the screen to search specifically for protocols that are not encrypted. Now just look around and see what sort of information you can find! Also check out this tutorial to learn how to read HTTP headers.
You may find information such as the operating system of the client computer and web browser that it’s running. This is the kind of information that you could be able to leverage to gain access later. When you’re done exploring, click on capture in the toolbar and select stop. The X icon will close the capture file. You can save it if you like (you will be prompted before it closes the file). Wireshark can do a lot more than what I’ve shown you in this basic tutorial. For more information refer to the Wireshark users guide and start experimenting!
Metasploit MSF Console and Armitage
As a newbie to hacking you learn to make use of msf console/metasploit. Armitage is a GUI program that allows you to scan for and perform exploits. Armitage’s visual interface can be a little more inviting to those who are new to a command line, and generally easier to use. There is certainly still a learning curve with Armitage.
The following video walks you through the steps to use an exploit called MS-08_067, which is actually the first exploit I learned when I was new to Kali. Be aware that Windows XP machines with security patches from 2008 or later will not be vulnerable to this particular attack. You’ll be using metasploit, Armitage, and nmap to execute the MS-08_067 exploit. The ultimate goal of this attack is to open a meterpreter shell.
Download our Nmap Essentials Cheat Sheet
Meterpreter is a dynamic extensible payload that uses in-memory DLL injection staggers to give you control over a target system. When I used this (in a virtual lab) I installed a keylogger, took screen shots, extracted files, and removed a critical system file that resulted in a failure to boot when the target machine was restarted. But it ran just fine until that point. You can do whatever you like once you’re in.
If you have trouble with the Windows XP meterpreter exploit, don’t get discouraged. There could be a number of reasons, and a Google search of where it stopped should help you along. Again, if your Windows XP machine has been patched after 2008, this exploit won’t work. In that case use some of the resources below to find tips, exploits, and legal to hack websites.
Now that you’ve got your feet wet with Kali Linux, it’s time for you to really start learning. Don’t get reliant on pre-built tools, and understand that you are essentially at this point running scripts or programs made by others. You should strive to understand what these tools are actually doing, and learn to create tools or scripts of your own. If you aspire to be an ethical hacker, you’ll need an intimate knowledge of computers, operating systems, networking, programming languages, and a bit of creativity.
subscribe by email
Stay Ahead
Related Posts
-
Cyber Security
Cybersecurity Mindful Moments by Tara Lemieux
February 7, 2023
-
Cyber Security
Boost your Cyber Security Awareness
December 13, 2021
-
Cyber Security
Why You Should Invest in Cyber Security
September 8, 2021