Trainers
There are several differences between CAP and RMF. While teaching these classes, I identified three major areas that require extra attention.
Authorization Decisions
The Interim Authority to Operate (IATO) is no longer used once an organization transitions from DIACAP to RMF. This appears to be a way to streamline the authorization process by eliminating one of the possible accreditation scenarios. It may also be an effort to close a “loophole” whereby some systems have remained in IATO status for an extended period. I heard stories from students about IATO systems that have been in production for several years at a time even though they have not been issued an ATO.
Those people familiar with the DIACAP C&A process are accustomed to requesting an Interim Authorization to Test (IATT) so that they can connect their system to the LAN for testing. This testing period typically lasts for 60 days. Any security issues identified during the IATT should be remediated before seeking an Authorization to Operate (ATO). This IATT decision effectively removes the less rigid constraints of the IATO, thereby tightening the overall authorization process.
Under DIACAP, an IATO may be issued in order to get the system one step closer to production. This IATO period can last for up to six months. Security weaknesses can be managed during this time period to better prepare for seeking the final ATO. Since RMF eliminates the IATO step, the system will remain in IATT mode from the time testing begins until it is ready for true production.
Mission Assurance Category (MAC) levels and Classification level (Classified, Sensitive, or Public)
The DoDI 8500.02 and CNSSI 1253 documents have been updated for use with RMF in order to modify certain instructions that formerly applied to the DIACAP C&A process. Several other NIST Special Publications have also been updated for the new framework. It may take some time for staff in IA positions to get used to the new terminology, but this is an important consideration if all Federal agencies will eventually follow the same standard.

Within RMF, the Mission Assurance Category levels (MAC I, II, or III) have been replaced by Impact Level (Low, Moderate, or High). All steps and tasks within the RMF-related documents now refer to Low, Moderate, and High instead of MAC I, II, or III. This now means that the System Categorization step at the beginning of the RMF now designates the Impact Level instead of MAC level for all subsequent tasks in the process.
The classification levels (Classified, Sensitive, or Public) have been replaced with Security Objectives (Confidentiality, Integrity, and Availability). The “high water mark” method may be used to categorize a system with an overall rating by reviewing the highest level determined for each Security Objective. (i.e. a system with Low Confidentiality, Moderate Integrity, and High Availability will have an overall Impact Level of High)
If the system is a National Security Systems (NSS), a more granular approach to categorization must be used. In these scenarios, each Security Objective is evaluated separately instead of using an overall rating. (i.e. Confidentiality is High, Integrity is Moderate, and Availability is Moderate).
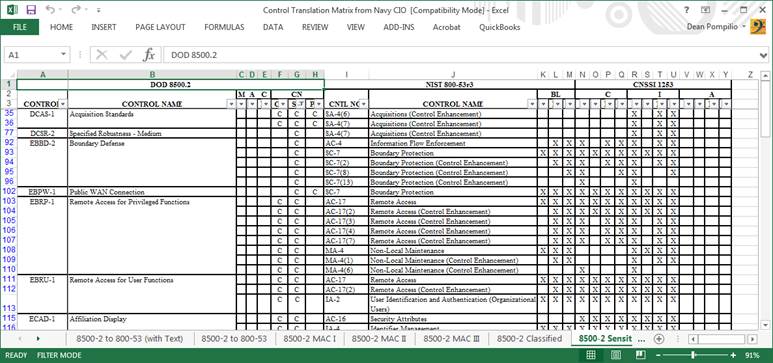
There are a few documents available which translate controls between 8500-series to NIST SP 800-53, or to MAC levels. The document shown below may prove very useful for organizations moving from DIACAP to RMF. I always provide this document to my students for their reference.
SDLC vs. C&A vs. A&A
The DIACAP Certification & Accreditation (C&A) process has changed into the RMF Assessment & Authorization (A&A) process. As a result, the IA professional now must understand the differences between all three frameworks while going through the overall process. The RMF places new emphasis on having a security mindset early in the A&A process. As a result, some tasks and steps have been reordered compared to the previous frameworks.
While teaching RMF, we spend time comparing the System Development Life Cycle (SDLC) to the RMF. As we go through each RMF task, the relevant SDLC phase is also discussed. The steps are structured differently than the SDLC, so we discuss how these frameworks line up side-by-side. Some activities occur in a different order within the RMF and it is important for the IA students to identify these changes.
The DIACAP C&A process also has some important differences when compared to the RMF. We spend time comparing these frameworks side-by-side so that the IA student can begin to learn how their activities will change under the RMF.
Changes to Roles and Terminology
Several roles or titles will change when transitioning to the RMF. The actual responsibilities may be the same, but the terminology has been updated for RMF. I have created a reference matrix to show which roles are changing:
| DIACAP Terms | RMF Terms |
| Designated Approving Authority (DAA) | Authorization Official (AO) |
| Senior Information Assurance Officer (SIAO) | Senior Information Security Officer (SISO) |
| DISN/GIG Flag Panel | DoD Information Security Risk Management Committee (DoD ISRMC) |
| DIACAP Technical Advisory Group (TAG) | RMF TAG |
| Information Assurance | Cybersecurity |
| DAA Representative (DAA Rep) | AO designated representative (AODR) |
| Certification Authority (CA) | Security Control Assessor (SCA) |
| System Identification Profile (SIP) and DIACAP Implementation Plan (DIP) | System Security Plan (SSP) |
| Scorecard, Evaluation Risk Report (ERR) | Part of the Security Assessment Report (SAR) |
| Validator (in the Army ACA) | Security Control Assessor (SCA) |
| Information Assurance Manager [responsibilities performed in the Army by the IAPM] | Information System Security Manager (ISSM) [combination of Army IAPM and Army IAM functions] |
| DIACAP Package | Security Authorization Package (SAP) |
| Mission Assurance Category (MAC) (included combined determination of integrity and availability levels) | Integrity and Availability determined separately |
subscribe by email
Stay Ahead
Related Posts
-
Cyber Security
Cybersecurity Mindful Moments by Tara Lemieux
February 7, 2023
-
Cyber Security
Boost your Cyber Security Awareness
December 13, 2021
-
Cyber Security
Why You Should Invest in Cyber Security
September 8, 2021